- Popis
- Detail
Popis
Forensic Express Pro
Vydání Pro je navrženo pro uživatele, kteří hledají pokročilé funkce – ideální pro všechny orgány činné v trestním řízení, průmyslové experty a forenzní profesionály.
Všechny funkce verze Standard plus:
Odblokování telefonu
Podpora iCloud
Rozpoznávání objektů na fotkách
Rozpoznávání obličejů
Detekce malwaru
Podpora Camera Ballistics
Podpora UFED
Integrace Access Data
Nový, rychlý a snadno použitelný software s dotykovým rozhraním pro zajištění dat z mobilních telefonů.
Zrychlete svou analýzu – s neuvěřitelnou jednoduchostí zajišťujte data z několika telefonů najednou a využijte pečlivě připravených templatů pro výstupní reporty.
Zajistěte data z mobilních zařízení
S aplikací Phone Forensics Express zajistíte všechny data jen pomocí pár kliknutí. Ve výsledku získáte nejen smazaná data, historii hovorů, kontakty, SMS, MMS, soubory, kalendář, poznámky, upomínky, ale i data z aplikací jako Skype, Dropbox, Evernote, Facebook, Whatsapp, Viber apod.
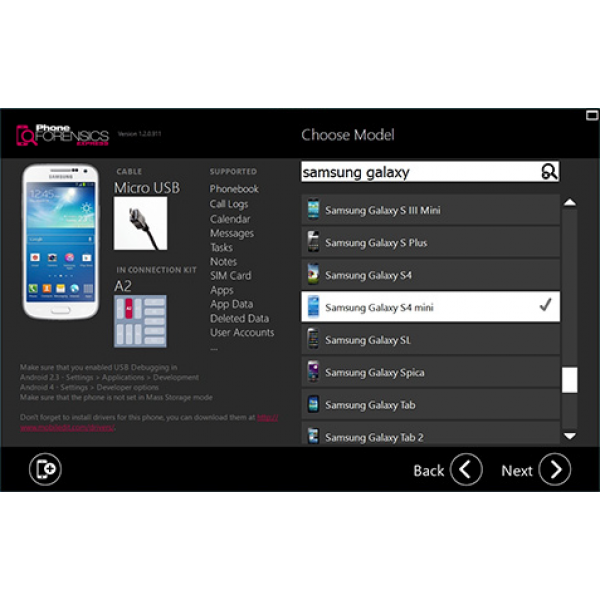
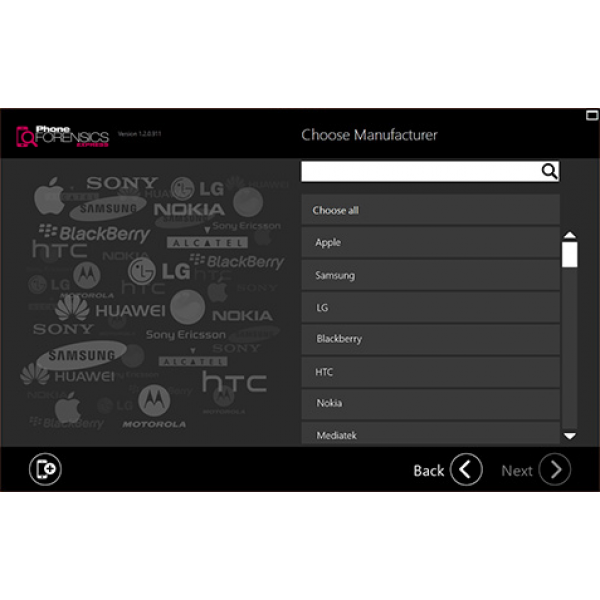
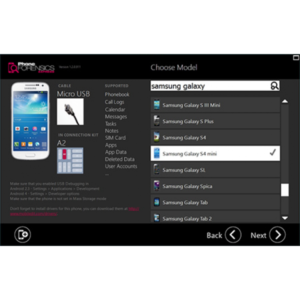
Rozsáhla podpora zařízení
Jako průkopníci v oblasti mobilní forenzní analýzy, nabízíme rozsáhlou podporu telefonů od roku 1996 až dodnes. V dnešní době náš software podporuje tisíce zařízení s operačními systémy, jako jsou například Android, iOS, Blackberry OS, Windows Phone, Windows Mobile, Symbian, Bada a Meego široké skupiny výrobců, jako např. Samsung, HTC, Nokia, Sony, LG, Motorola a mnoha čínských značek. Nástroj si rovněž poradí s celou řadou starších telefonů bez OS.
Zajištění dat z aplikací
Využívání aplikací pro komunikaci a sdílení obsahu zažívá obrovský růst. Mnoho aplikací vzniká nebo je updatováno prakticky denně. Je evidentní, že analýza aplikací je klíčová pro zajištění všech relevantních informací ze zařízení.
Analýza aplikací je nejsilnější stránkou Phone Forensics Express. Velká část našeho týmu se věnuje problematice aplikací a jsme tak schopni stále přidávají podporu i pro ty nejnovější. Forensics Express provádí hloubkovou analýzu dat, zajišťující všechna dostupná data aplikací včetně těch smazaných. Získaná data jsou podrobena analýze obsahu a vy si je tak můžete zobrazit na časové ose jako poznámky, fotografie či konverzace bez ohledu na to, kterou aplikací byla tato data vytvořena.
Zajišťujte data na několika zařízeních najednou
Zajištění dat z mobilních zařízení zabírá mnoho času. Zrychlete svou práci připojením několika telefonů najednou. Jediné co potřebujete je USB hub, kabely a počítač s nainstalovaným nástrojem Phone Forensics Express.
Několik výstupních formátů najednou
Zvolte si váš oblíbený formát a závěrečnou zprávu exportujte přesně v tom formátu, jaký se vám hodí. Nabízí se vám formáty jako PDF, XLS, nebo HTML s náhledem celého obsahu na daném zařízení. Můžete si rovněž vytvořit závěrečnou zprávu ve formátu XLS, která bude kompatibilní se ostatními forenzními nástroji, které využíváte.
Bypass zámku obrazovky na iOS
Přestože má iOS velmi dobře zabezpečená data, Forensics Express dokáže prolomit zabezpečení a data dešifrovat. Jsou k tomu potřeba pouze Lockdown soubory ze spárovaného počítače. Tyto soubory jsou vytvořeny ve chvíli, kdy připojíte své zařízení iOS ke svému počítači a autorizujete ho. Díky souborům Lockdown budete schopni obnovit všechna data z telefonu, i když bude zamčený.
Data ze starých záloh
Phone Forensics Express dokáže zajistit data ze starých záloh. To se hodí, když nemůžete použít konkrétní telefon, ale máte přístup k datům z autorizovaného počítače.
Obnovte veškeré informace ze SIM karty
Forensics Express vám pomůže k získání ICCID bez kódu PIN a také k zjištění oblasti, ze které karta pochází (Location Area Information). Budete mít také možnost dostat se k datům, jako jsou kontakty, zprávy, IMSI a nebo seznam používaných aplikací na SIM kartě.
Jednoduchý proces připojení zařízení
Naše databáze mobilních zařízení a snadno použitelné prostředí vám usnadní práci. Okamžitě uvidíte všechny informace, které potřebujete: kompletní funkce telefonu, kompatibilní kabely, ovladače a potřebné návody.
Updaty
Softwarové updaty jsou v dnešní době neustálého vývoje nutné. Stále přidáváme nová zařízení a analyzujeme nové aplikace. Nejnovější updaty vám tak dávají vždy ty nejširší možnosti využití. Nový nástroj jsme odladili i díky obrovské odezvě uživatelů MOBILeditu. Díky tomu máme jistotu, že Phone Forensics Express nabídne ty nejlepší funkce s podporou nejvíce mobilních zařízení.
Analyzujte rychle a jednoduše
Už nemusíte být expertem v oblasti forenzní analýzy, abyste dokázali zajistit data na mobilním zařízení. S naším softwarem to dokáže každý. Je intuitivní, dokáže jednoduše zajistit data a s vylepšenou autodetekcí snižuje nároky na znalosti postupů.
Vyvinuto v EU
Naší klíčovou výhodou je umístění našeho výzkumného a vývojového centra v Praze, což spolu s vysokými standardy kvality podporuje rozsah našich schopností v oblasti fyzické analýzy v Evropě prodávaných telefonů.
Mnohaleté zkušenosti
Firma Compelson Labs byla založena v roce 1991 a od roku 1996 nabízí nástroje pro mobilní forenzní analýzu. Náš předchozí produkt MOBILedit byl velmi dobře hodnocen National Institute of Standarts and Technology a je stále používaný FBI, CIA, IRS a bezpečnostními složkami více než 75 zemí světa.
Main Functions
Phone extractor with extremely wide range of supported phones
Password breaker with GPU acceleration and multi-threaded operation for maximum speed
iTunes backup analyzer
Android ADB backup analyzer
Applications data analyzer
Photo Recognizer
Deleted data recovery
Cellebrite UFED data analyzer
Cellebrite UFED data generator
Oxygen data analyzer
Report generator
Phone unlocking
Connecting phones
The phone connection wizard will guide you through simple to follow instructions allowing even a novice to work with the product. It also eliminates stress by showing you which setting you need and what buttons to press to make sure your phone connects every time.
Open/Import files
iTunes backup
Android ADB backup
MOBILedit Backup XML
Oxygen Export XML
Cellebrite UFDR
Cellebrite UFD with both, logical data and physical images (new in version 4.0)
Exports and reports
HTML – creates site structure for easy data browsing using any browser
PDF – Acrobat reader single file or multiple files
XML – Excel
XLS – Excel workbook
UFDR – Cellebrite report file
MOBILedit export structure of files with parsed data from phone
MOBILedit backup structure of raw files from phone
MOBILedit export and backup can be compressed and encrypted using AES and protected by MD5 or SHA256 hashes.
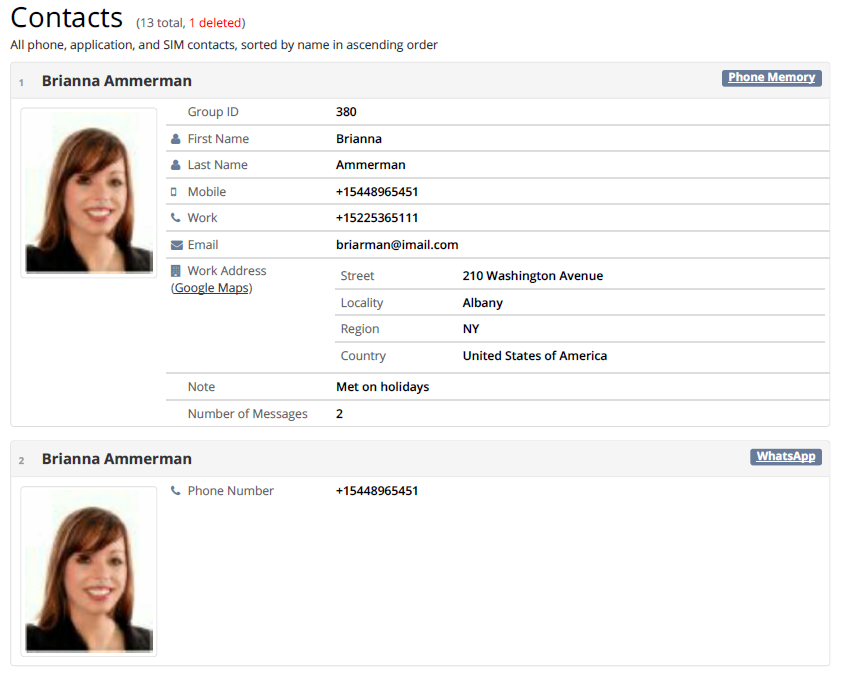
Contacts
Three unique reports help uncover the suspect’s connections.
The Contacts Report presents all contact details fully retrieved and analyzed, including deleted contact details when available. Contact recovery scope is from multiple sources such as phonebook and memory, vCard files, SIM card, cloud accounts and applications. Search a report directly for names, numbers, deleted contacts or other information. The report informs the investigator when the contact was created, when it was last modified and which account type it is (WhatsApp, Cloud, Gmail, Facebook etc.). Find important information such as phone numbers, email address, home address, birthday, employer, and contact profile pictures to help you put a face to a name.
With a Contact Analysis Report find out who the suspect has been in contact with the most, and discover crucial connections. Contact Analysis will detail the number of sent and received messages and calls including total minutes of talk-time for each contact, sorted in descending order by the number of communication events with the suspect.
The Contact Accounts Report will help the investigator find all phone, email, cloud and applications accounts associated with the suspect’s device.
Messages
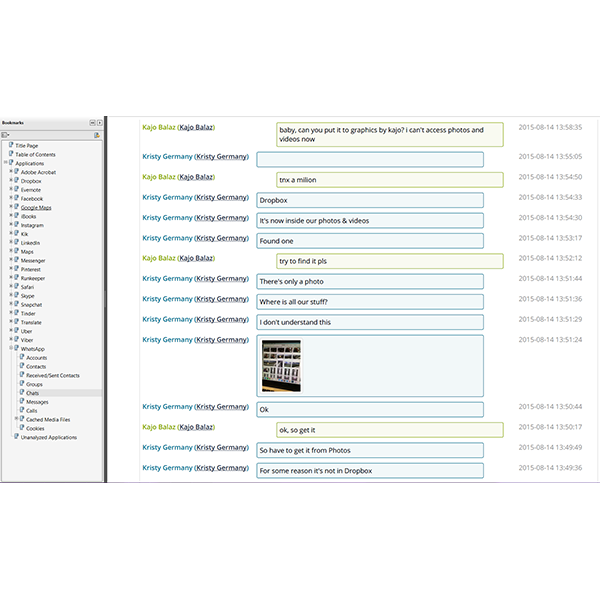
Messages are fully retrieved for analysis and presented in the Messages Report, including deleted messages when available. Messages include standard phone messages (SMS, MMS, iMessages), email messages, SIM messages and application messages. Customize the report and sort by contact, timeline, conversation view, or both.
Conversations
Efficiently read through entire uninterrupted conversation streams. The Conversations Reports separates entire conversations by contact and are ordered by time sequence. Captured conversations include all SMS, MMS, iMessages and applications messages including encrypted-messaging apps.
Call Logs
The Calls Report provides details of all mobile service and applications-based phone calls, including deleted calls. Pin-point the time and date of when the suspect made or received calls, the duration of the call, the source (mobile, Facebook, WhatsApp etc.) and the contact and phone number associated with each call.
Emails
Emails are fully retrieved for analysis and presented in the Emails Report, including deleted messages when available. Customize the report and sort by contact, timeline, conversation view, or both.
Applications
Perform an advanced applications analysis. All applications are listed and fully analyzed for their detailed data, including deleted applications data where available, and presented in the Applications Report. Narrow your search by selecting the specific applications you wish to analyze, or complete an analysis on all applications in the device. Criminals, terrorists and everyday people are using encrypted-messaging applications more than ever, now an investigator can read these messages. Raw application data are also stored in the export folder, which makes additional processing and analysis possible. We support hundreds of applications and the list is growing.
Integrate
We understand an investigator may use many tools in an investigation. We’ve designed our software with the ability to integrate with other forensic tools in your lab. Import and analyze data files exported from Cellebrite UFED and Oxygen reports to uncover potentially overlooked data. Export all MOBILEdit Forensic Express data to UFED, so you can use the UFED Viewer or Analytics for further processing to move your investigation forward.
Deleted Data
Deleted data is often the key information in an investigation. Deleted data details are presented in a special comprehensive Deleted Data Report, and also displayed within each individual analysis report. Whether it is calls, SMS, MMS, calendar events, notes, applications data, or other evidence your are looking for, MOBILedit Forensic Express searches deeply in databases for caches and hidden files to reveal the maximum deleted data possible.
Passwords
The Passwords Report will reveal passwords from many types of accounts and applications.
In iOS devices all system passwords and most application passwords are managed through dedicated and encrypted Keychain. We are able to decrypt the keychain and retrieve all passwords that were saved in it. Passwords contained in the Keychain include: Wi-Fi passwords, appleID password, passwords saved in Safari as well as various email and application passwords, and passwords saved in web browsers and other accounts. From Android devices Wi-Fi passwords are retrieved.
Wi-Fi Networks
This section contains detailed data about all Wi-Fi networks saved in a device. The Wi-Fi Networks Report displays the history of Wi-Fi connections in time sequential order, including the Wi-Fi network name, the last joined time and date, the last auto-joined time and date (indicates that a suspect has been a repeat visitor to the network location), SSID, BSSID, and security mode. Supported are also continued logs – connected time. Even Wi-Fi network passwords are recovered and are shown in Password Report.
Images
The Images Report will contain images from the phone file system. This includes application images – images retrieved from applications data, which might also include images stored in temporary files or caches that have been detected as potential images. An option to display large images in full size will create an additional section in the report and display one image per page. Filter out duplicate images to omit emoticons and similar images from the reports.
Photos
The Photos Report retrieves all device and applications photos taken by the phone, usually in the DCIM folder. iPhone deleted photos can be recovered if they were sent via MMS or from a supported application. The ability to recover deleted photos depends on many internal factors in the storage and cannot be predicted nor guaranteed. Supported is also an Apple photo format HEIF.
Cell towers
Data about cell towers that the subject phone was connected to can be obtained. Obtained cell tower locations can be individually viewed on the map through the provided link.
Audio Files
Audio files are copied from the device and its applications. The Audio Files Report allows you to play an audio file simply by clicking on it in the report. The report also details the file path, the created and modified time, the duration of the audio file and the size of the audio file.
Video Files
Video files are also copied from the device and its applications. The Video Files Report allows you to play a video file by clicking on it in the report. The report also details the file path, the created, modified, encoded and tagged time, the duration of the video, the size of the video file as well as the frame rate, height and width.
Organizer
The device and applications organizers are searched and analyzed, and data is presented in four distinct reports. Customize the search within a specific timeframe for calendar events, notes and tasks, or complete a full phone search.
The Calendar Accounts Report displays the various device and applications accounts where events are created and stored. Details include the account source, name, account owner, account email address and the number of associated events with the calendar.
An Events Report lists all events in detail from the device and its applications, including deleted events from calendars and other sources where events are created. Details include which calendar the event was created in, a summary, a description, start time, created time, modified time, end time, recurrence, if the event was removed or deleted and are sequenced in ascending or descending order.
Tasks are carefully compiled and presented in detail in the Tasks Report. Tasks found in the device and applications include the full task text content, the creation time, modified time, start time, completion time and indicates if the task was deleted.
Notes including deleted or removed notes are compiled in detail in the Notes Report. Gathered from the device and applications, the report includes a header title, a summary, the full text content of the note, the created, modified and last visit time, as well as if the note was removed or deleted.
Documents
Extract and preview most common document formats.
GPS Locations
Knowing when and where a suspect has been is key in every investigation. The GPS Locations Report contains all possible GPS location data from the device and applications. We are able to extract ‚last known‘ locations from Android devices. The analysis and report yield valuable information from map, fitness and transportation applications such as Google Maps, Pokémon Go, Nike+ Running, Uber and many more. Some applications may even contain GPS data about the entire route, and show the sequence of GPS coordinates with their timestamps recorded and stored. Photos and videos on a device may also contain GPS locations in their metadata. Customize the locations search and report by time, or search and order locations by proximity to specific GPS coordinates.
Cookies
The Cookies Report compiles the history of cookies in a device. System cookies are only obtainable from iOS devices. Application specific cookies are analyzed for every installed application. Cookies contain information about web domain as well as their creation, accessed and expiration time, and if the displayed cookie has been deleted.
Web Browsing History
The Web Browsing History Report contains a consolidated web browsing history from all analyzed browser applications. Each web browsing history entry consists of the visited URL as well as time of the visit. In some cases the total number of visits of the URL is also available with the timestamps of individual visits. The report is customizable by alphabetical order or by time sequence.
Web Search History
The Web Search History Report contains queries searched in the web browser as well as a timestamp of when the search occurred. System-wide web searches are only obtainable from Android 5.1 devices and older. Web search data is also gathered from browser application analysis.
Bluetooth Pairings
Bluetooth pairing history can be discovered on both Android and iOS devices and is presented in the Bluetooth Pairings Report. In the report you will find the name of the Bluetooth connection, the Bluetooth address of the pairing device, the status, and on iOS- the date and time of the last connection.
Contact analysis
Contact analysis is a section with analyzed relationships between contacts and the way they were used in various modes of communication. It is also possible to skip contacts that have rarely been communicated with on that mobile phone.
Notifications
Notifications of the device and applications are presented in detail and are retrievable from iOS and Android devices. The Notifications Report displays notifications information including the source, the text of the notification, and the timestamp. On iOS also included are notifications that are no longer active and may contain otherwise unobtainable information, such as emails and messages from applications that do not store them in databases. On Android only active notifications are retrievable.
Bookmarks
The Bookmarks Report gathers device and application global browser bookmarks on iOS devices (Safari bookmarks), and on Android devices up to Android 5.1; later versions of Android only application specific bookmarks can be obtained. The report can be sorted by time or name in alphabetical order.
Keyboard Cache
The Keyboard Cache Report contains all words that have been typed on device and is only available on devices running iOS version 7 and older. On Android devices we can extract User Dictionary that contains custom user defined words
System Logs
The System Logs Report contains system logs and dumpsys files that can be extracted from Android phones. The Android system keeps these files for debugging and monitoring purposes and they contain system data such as recent locations, recent connected Wi-Fi networks, running applications, recently launched applications, recent cell locations and signal info, current Bluetooth MAC address and name etc. These files are listed in the System Logs section within the HTML and PDF reports and can be directly opened by clicking on their filenames. Their content is analyzed and presented in various reports such as Wi-Fi Networks, GPS Locations, Notifications etc.
File System
The File System Report is divided in three section according their source. Internal – which includes raw file system. Then Application File System which contains application data files. The third is the Extra File System, which contains information about files that are not physically present on device but are available to be extracted. This includes all files from iTunes backup on iOS devices. On Android devices, Content Providers, System Logs and DumpSys fall into this category.
Timeline
The Timeline Report provides insight into all device activity exactly as it occurred. The report aggregates all extracted items that contain time and date information and displays it in chronological order. Exact parameters of a generated timeline can be customized to specific function; for example, you can select to configure a timeline of calls and messages only.
Photo Recognizer
This module automatically locates and recognizes suspicious content in photos such as weapons, drugs, nudity, currency and documents. Photo Recognizer utilizes artificial intelligence and deep machine learning to quickly analyze an unlimited number of photos, and is designed to eliminate countless hours that would be spent manually searching for key evidence in huge databases of photos. Each photo is placed in its own specific category so the investigator can keep the case well-organized and easily present the suspicious content in a fine-tuned report.
Phone Unlocking
For a wide range of Android devices, the phone unlocking feature allows for physical image acquisition even when the device is protected by a password or gesture, also able to bypass the lock-screen with many phone models.
xtremely wide range of supported phones
-
Password breaker with GPU acceleration and multi-threaded operation for maximum speed
-
iTunes backup analyzer
-
Android ADB backup analyzer
-
Applications data analyzer
-
Photo Recognizer
-
Deleted data recovery
-
Cellebrite UFED data analyzer
-
Cellebrite UFED data generator
-
Oxygen data analyzer
-
Report generator
-
Phone unlocking
Connecting phones
The phone connection wizard will guide you through simple to follow instructions allowing even a novice to work with the product. It also eliminates stress by showing you which setting you need and what buttons to press to make sure your phone connects every time.
Open/Import files
iTunes backup
Android ADB backup
MOBILedit Backup XML
Oxygen Export XML
Cellebrite UFDR
Cellebrite UFD with both, logical data and physical images (new in version 4.0)
Exports
and
reports
HTML – creates site structure for easy data browsing using any browser
PDF – Acrobat reader single file or multiple files
XML – Excel
XLS – Excel workbook
UFDR – Cellebrite report file
MOBILedit export structure of files with parsed data from phone
MOBILedit backup structure of raw files from phone
MOBILedit export and backup can be compressed and encrypted using AES and protected by MD5 or SHA256 hashes.
Contacts
Three unique reports help uncover the suspect’s connections.
The Contacts Report presents all contact details fully retrieved and analyzed, including deleted contact details when available. Contact recovery scope is from multiple sources such as phonebook and memory, vCard files, SIM card, cloud accounts and applications. Search a report directly for names, numbers, deleted contacts or other information. The report informs the investigator when the contact was created, when it was last modified and which account type it is (WhatsApp, Cloud, Gmail, Facebook etc.). Find important information such as phone numbers, email address, home address, birthday, employer, and contact profile pictures to help you put a face to a name.
With a Contact Analysis Report find out who the suspect has been in contact with the most, and discover crucial connections. Contact Analysis will detail the number of sent and received messages and calls including total minutes of talk-time for each contact, sorted in descending order by the number of communication events with the suspect.
The Contact Accounts Report will help the investigator find all phone, email, cloud and applications accounts associated with the suspect’s device.
Messages
Messages are fully retrieved for analysis and presented in the Messages Report, including deleted messages when available. Messages include standard phone messages (SMS, MMS, iMessages), email messages, SIM messages and application messages. Customize the report and sort by contact, timeline, conversation view, or both.
Conversations
Efficiently read through entire uninterrupted conversation streams. The Conversations Reports separates entire conversations by contact and are ordered by time sequence. Captured conversations include all SMS, MMS, iMessages and applications messages including encrypted-messaging apps.
Call Logs
The Calls Report provides details of all mobile service and applications-based phone calls, including deleted calls. Pin-point the time and date of when the suspect made or received calls, the duration of the call, the source (mobile, Facebook, WhatsApp etc.) and the contact and phone number associated with each call.
Emails
Emails are fully retrieved for analysis and presented in the Emails Report, including deleted messages when available. Customize the report and sort by contact, timeline, conversation view, or both.
Applications
Perform an advanced applications analysis. All applications are listed and fully analyzed for their detailed data, including deleted applications data where available, and presented in the Applications Report. Narrow your search by selecting the specific applications you wish to analyze, or complete an analysis on all applications in the device. Criminals, terrorists and everyday people are using encrypted-messaging applications more than ever, now an investigator can read these messages. Raw application data are also stored in the export folder, which makes additional processing and analysis possible. We support hundreds of applications and the list is growing.
Integrate
We understand an investigator may use many tools in an investigation. We’ve designed our software with the ability to integrate with other forensic tools in your lab. Import and analyze data files exported from Cellebrite UFED and Oxygen reports to uncover potentially overlooked data. Export all MOBILEdit Forensic Express data to UFED, so you can use the UFED Viewer or Analytics for further processing to move your investigation forward.
Deleted Data
Deleted data is often the key information in an investigation. Deleted data details are presented in a special comprehensive Deleted Data Report, and also displayed within each individual analysis report. Whether it is calls, SMS, MMS, calendar events, notes, applications data, or other evidence your are looking for, MOBILedit Forensic Express searches deeply in databases for caches and hidden files to reveal the maximum deleted data possible.
Passwords
The Passwords Report will reveal passwords from many types of accounts and applications.
In iOS devices all system passwords and most application passwords are managed through dedicated and encrypted Keychain. We are able to decrypt the keychain and retrieve all passwords that were saved in it. Passwords contained in the Keychain include: Wi-Fi passwords, appleID password, passwords saved in Safari as well as various email and application passwords, and passwords saved in web browsers and other accounts. From Android devices Wi-Fi passwords are retrieved.
Wi-Fi Networks
This section contains detailed data about all Wi-Fi networks saved in a device. The Wi-Fi Networks Report displays the history of Wi-Fi connections in time sequential order, including the Wi-Fi network name, the last joined time and date, the last auto-joined time and date (indicates that a suspect has been a repeat visitor to the network location), SSID, BSSID, and security mode. Supported are also continued logs – connected time. Even Wi-Fi network passwords are recovered and are shown in Password Report.
Images
The Images Report will contain images from the phone file system. This includes application images – images retrieved from applications data, which might also include images stored in temporary files or caches that have been detected as potential images. An option to display large images in full size will create an additional section in the report and display one image per page. Filter out duplicate images to omit emoticons and similar images from the reports.
Photos
The Photos Report retrieves all device and applications photos taken by the phone, usually in the DCIM folder. iPhone deleted photos can be recovered if they were sent via MMS or from a supported application. The ability to recover deleted photos depends on many internal factors in the storage and cannot be predicted nor guaranteed. Supported is also an Apple photo format HEIF.
Cell towers
Data about cell towers that the subject phone was connected to can be obtained. Obtained cell tower locations can be individually viewed on the map through the provided link.
Audio Files
Audio files are copied from the device and its applications. The Audio Files Report allows you to play an audio file simply by clicking on it in the report. The report also details the file path, the created and modified time, the duration of the audio file and the size of the audio file.
Video Files
Video files are also copied from the device and its applications. The Video Files Report allows you to play a video file by clicking on it in the report. The report also details the file path, the created, modified, encoded and tagged time, the duration of the video, the size of the video file as well as the frame rate, height and width.
Organizer
The device and applications organizers are searched and analyzed, and data is presented in four distinct reports. Customize the search within a specific timeframe for calendar events, notes and tasks, or complete a full phone search.
The Calendar Accounts Report displays the various device and applications accounts where events are created and stored. Details include the account source, name, account owner, account email address and the number of associated events with the calendar.
An Events Report lists all events in detail from the device and its applications, including deleted events from calendars and other sources where events are created. Details include which calendar the event was created in, a summary, a description, start time, created time, modified time, end time, recurrence, if the event was removed or deleted and are sequenced in ascending or descending order.
Tasks are carefully compiled and presented in detail in the Tasks Report. Tasks found in the device and applications include the full task text content, the creation time, modified time, start time, completion time and indicates if the task was deleted.
Notes including deleted or removed notes are compiled in detail in the Notes Report. Gathered from the device and applications, the report includes a header title, a summary, the full text content of the note, the created, modified and last visit time, as well as if the note was removed or deleted.
Documents
Extract and preview most common document formats.
GPS Locations
Knowing when and where a suspect has been is key in every investigation. The GPS Locations Report contains all possible GPS location data from the device and applications. We are able to extract ‚last known‘ locations from Android devices. The analysis and report yield valuable information from map, fitness and transportation applications such as Google Maps, Pokémon Go, Nike+ Running, Uber and many more. Some applications may even contain GPS data about the entire route, and show the sequence of GPS coordinates with their timestamps recorded and stored. Photos and videos on a device may also contain GPS locations in their metadata. Customize the locations search and report by time, or search and order locations by proximity to specific GPS coordinates.
Cookies
The Cookies Report compiles the history of cookies in a device. System cookies are only obtainable from iOS devices. Application specific cookies are analyzed for every installed application. Cookies contain information about web domain as well as their creation, accessed and expiration time, and if the displayed cookie has been deleted.
Web Browsing History
The Web Browsing History Report contains a consolidated web browsing history from all analyzed browser applications. Each web browsing history entry consists of the visited URL as well as time of the visit. In some cases the total number of visits of the URL is also available with the timestamps of individual visits. The report is customizable by alphabetical order or by time sequence.
Web Search History
The Web Search History Report contains queries searched in the web browser as well as a timestamp of when the search occurred. System-wide web searches are only obtainable from Android 5.1 devices and older. Web search data is also gathered from browser application analysis.
Bluetooth Pairings
Bluetooth pairing history can be discovered on both Android and iOS devices and is presented in the Bluetooth Pairings Report. In the report you will find the name of the Bluetooth connection, the Bluetooth address of the pairing device, the status, and on iOS- the date and time of the last connection.
Contact analysis
Contact analysis is a section with analyzed relationships between contacts and the way they were used in various modes of communication. It is also possible to skip contacts that have rarely been communicated with on that mobile phone.
Notifications
Notifications of the device and applications are presented in detail and are retrievable from iOS and Android devices. The Notifications Report displays notifications information including the source, the text of the notification, and the timestamp. On iOS also included are notifications that are no longer active and may contain otherwise unobtainable information, such as emails and messages from applications that do not store them in databases. On Android only active notifications are retrievable.
Bookmarks
The Bookmarks Report gathers device and application global browser bookmarks on iOS devices (Safari bookmarks), and on Android devices up to Android 5.1; later versions of Android only application specific bookmarks can be obtained. The report can be sorted by time or name in alphabetical order.
Keyboard Cache
The Keyboard Cache Report contains all words that have been typed on device and is only available on devices running iOS version 7 and older. On Android devices we can extract User Dictionary that contains custom user defined words
System Logs
The System Logs Report contains system logs and dumpsys files that can be extracted from Android phones. The Android system keeps these files for debugging and monitoring purposes and they contain system data such as recent locations, recent connected Wi-Fi networks, running applications, recently launched applications, recent cell locations and signal info, current Bluetooth MAC address and name etc. These files are listed in the System Logs section within the HTML and PDF reports and can be directly opened by clicking on their filenames. Their content is analyzed and presented in various reports such as Wi-Fi Networks, GPS Locations, Notifications etc.
File System
The File System Report is divided in three section according their source. Internal – which includes raw file system. Then Application File System which contains application data files. The third is the Extra File System, which contains information about files that are not physically present on device but are available to be extracted. This includes all files from iTunes backup on iOS devices. On Android devices, Content Providers, System Logs and DumpSys fall into this category.
Timeline
The Timeline Report provides insight into all device activity exactly as it occurred. The report aggregates all extracted items that contain time and date information and displays it in chronological order. Exact parameters of a generated timeline can be customized to specific function; for example, you can select to configure a timeline of calls and messages only.
Photo Recognizer
This module automatically locates and recognizes suspicious content in photos such as weapons, drugs, nudity, currency and documents. Photo Recognizer utilizes artificial intelligence and deep machine learning to quickly analyze an unlimited number of photos, and is designed to eliminate countless hours that would be spent manually searching for key evidence in huge databases of photos. Each photo is placed in its own specific category so the investigator can keep the case well-organized and easily present the suspicious content in a fine-tuned report.
Phone
Unlocking
For a wide range of Android devices, the phone unlocking feature allows for physical image acquisition even when the device is protected by a password or gesture, also able to bypass the lock-screen with many phone models.